vpntraffic.com-The fastest and easiest way to secure your internet connection and unblock any website. Works with PCs, Macs, and phones.
Saturday, March 31, 2012
How to watch UK/British television in Greece
Thursday, March 29, 2012
If your users are already using the Juniper SSL VPN
If your users are already using the Juniper SSL VPN solution today, using just an Active Directory username and password, you need to decide the migration path: Force everyone to use Digipass from day 1So once you have configured everything it will be impossible for users to work remotely if they do NOT have their Digipass. This is probably very hard to do unless you have a small number of users, and you can hand over the Digipass to all of them at the same time. Allow a few days/weeks of "transition" periodYou allow users to work remotely using their username and password for a few more days. Once they login with their Digipass for the first time, they are forced on using it every time in the future. Most organisation will choose for this option, since it will guarantee a smooth transition without users complaining they cannot work!2.3.1. Convincing usersNote that some people may ask for a 3rdoption, where they can work remotely without their Digipass even after they have successfully used the Digipass. This is a normal reaction since people have been used to work without this device for some time. They see it as a "burden": now they have to make a habit of always having the Digipass in their pocket...Obviously the whole point of implementing Digipass authentication is to improve security, so make sure you explain the users "why" this is so important.Do NOT give in, even if your manager or the big boss tells you to make an exception. If some users have the privileged of working remotely without Digipass, the solution makes no sense! Don't forget that the high level executives are the ones with access to the most sensitive information.
Bypassing Throttling Using Protocol
Kindle Fire vpn
Wednesday, March 28, 2012
VPN Error 800:
Tuesday, March 27, 2012
VPN Error 913 solution
Sunday, March 25, 2012
Buy Kazakhstan KZ VPN Service - Fast, Reliable and Secure!
Buy Qatar QA VPN Service - Fast, Reliable and Secure!
Saturday, March 24, 2012
SLL/ VPN solution
productivity benefits, but security risks have increased accordingly", states Ajay Kumar Meher, CIO at Multi Screen Media Pvt. Ltd. "Static passwords are extremely inadequate for remote and mobile users; posing vast risks as they can be easily guessed or hacked. We therefore quickly decided to deploy strong two-factor authentication; a much more secure means of authenticating users onto networks as it requires two separate security elements."DIGIPASS TECHNOLOGY IS 'BEST FIT'After conducting a requirements analysis, MSM evaluated a number of twofactor authentication solutions from various vendors. Ultimately, MSM decided on VASCO's DIGIPASS technology as the solution was the 'best fit' for its security needs."VASCO's authentication solutions distinguished itself from competitors, due to its low total cost of ownership", Ajay Kumar Meher said. "The DIGIPASS technology could be seamlessly integrated into our existing SLL/ VPN solution. What's more, we were not required to buy additional costly, specialized hardware or to install supplementary software on end-users' PCs.""Furthermore, VASCO's DIGIPASS devices are very cost-effective as they have an extended battery lifetime of up to seven years, depending on use. We can gradually replace the devices as they expire, spreading costs and reducing logistic issues as we don't need to replace the devices all at once."The integration process of VASCO's authentication solution into MSM's SSL/VPN solution went quite smoothly. "We experienced some minor issues during the set-up phase, but these were quickly solved thanks to VASCO's professional support services. No other issues occurred during the implementation and rollout phase. All in all, everything went surprisingly well", said Ajay Kumar Meher
Friday, March 23, 2012
larger VPN handoff
achieved. In the real world experiment, a larger VPN handoff time was measured and analysed. This thesis also gives some suggestion of how to reduce the handoff time in the real world which may open a range of new research opportunities. One journal paper and one conference paper related to this thesis have been published: C. Xu and P. Radcliffe, "Building Secure Tunnel from PPP Wireless Network", Wireless Personal Communications, DOI 10.1007/s11277-009-9894-x, 2009. C. Xu and P. Radcliffe, "A novel mobility solution based on L2TP/IPsec tunnel", 2009 IEEE Sarnoff Symposium, 2009. 1.3 LITERATURE SEARCH The most common solution to mobility problems in a VPN is to run tunnels, such as L2TP or IPsec, over Mobile IP (double tunneling) [21, 22]. However, that is inefficient due to the overhead of network traffic (see Chapter 8.4). The packet structures of these tunnels are shown below. Figure 1-2 Packet Structures of Double Tunneling Some solutions [19, 53] are to add mobility support only to IPsec. These solutions can only transfer IP packets (Layer 3 packet). If user wants to send Layer 2 packets (such as PPP packets [39]), an IPsec tunnel cannot provide a solution. Furthermore, these solutions lose packets as they do not provide a method for sending old packets to the new IP address, and have relatively lower performance when handling handoff. Synchronization problems may also occur when the IPsec server updates tunnel information and sends IPsec packets at the same time. Some solution [19] also has security problems. A detailed analysis of these solutions will be shown in Chapter 8.4.
Thursday, March 22, 2012
Complete VPN Content
Application ControlApplication control enables you to define and enforce policies for thousands of applications running on your network and endpoints. Newer Web-based applications such as Facebook, Skype, Twitter and Salesforce.com can be detected and controlled at a granular level, regardless of ports and protocols used. Application classification and control is essential to manage the explosion of new Internet-based technologies bombarding networks today. Wireless ControllerAll FortiGate and FortiWiFi™ consolidated security platforms have an integrated wireless controller, enabling centralized management of FortiAP™ secure access points and wireless LANs. Unauthorized wireless traffic is blocked, while allowed traffic is subject to identity-aware multi-threat security inspection. You can control network access, quickly update security policies, and identify and suppress rogue access points - all from a single console.FortiOS 4.0 Software — Complete VPN Content and Network ProtectionFortinet continues to increase the breadth and depth of security and networking services included in the FortiOS purposebuilt operating system. By adding new functionality and enhancing the performance of existing services, FortiOS software continues to demonstrate why it remains the gold standard for multi-threat security. FortiOS 4.0 software includes many advanced security and networking features, some of which are highlighted below:Web FilteringInappropriate Web surfing and use of Web-based applications can result in lost productivity, network congestion, malware infection and data loss. Web Filtering controls user access to Webbased applications such as instant messaging, peer-to-peer file sharing and streaming media, while blocking phishing sites and blended network attacks. In addition, botnet command and control traffic and fast flux file downloading can be blocked. Flow-based Web filtering options are available.
Wednesday, March 21, 2012
MGM VPN Holdings
The industry may become more consolidated if the Comcast-NBC Universal merger is approved. Today, for example, Comcast owns E! Entertainment Television, Versus, The Golf Channel, regional sports networks, G4, and invests in The Style Network, TV One, PBS Kids Sprout,23Current, Driver TV, MGM VPN Holdings, NHL Network, Music Choice, Pittsburgh Cable News Channel LLC, and the MLB (Major League Baseball) Network. If the Comcast-NBC merger is approved, then Comcast would also own MSNBC, CNBC, Bravo, USA Network, Sci-Fi, the NBC network (which affiliates with hundreds of broadcast stations), Telemundo and a minority share in broadcaster ION media, as well as more than 20 local NBC-owned-and-operated broadcast stations and a major interest in the online video service Hulu. Comcast also has disclosed its equity interests in several smaller cable programmers.24In a common practice that further increases vertical integration, cable TV distributors require small programmers to give up much of their companies' equity stock to cable TV distributors just to get carried.25 As one programmer's CEO explained, "Cable and satellite TV companies want to own you before they put you on television."26 If true, this is illegal under communications laws.27Programmers have argued that distributors collectively blackball any programmer who files a
Tuesday, March 20, 2012
Netflix usa vpn outside iphone
Tech also lies at the heart of the warehouse operations that deliver customer satisfaction and enhance brand value. As mentioned earlier, brand is built through customer experience, and a critical component of customer experience is for subscribers to get their DVDs as quickly as possible. In order to do this, Netflix has blanketed the country with a network of over 50 ultrahigh-tech distribution centers that collectively handle in excess of 1.8 million DVDs a day. These distribution centers are purposely located within driving distance of 119 U.S. Postal Service processing & distribution facilities. By 4 a.m. each weekday, Netflix trucks collect the day's DVD shipments from these U.S.P.S. hubs and returns the discs to the nearest Netflix center. DVDs are fed into custom-built sorters that handle disc volume on the way in and the way out. Most DVDs never hit the re-stocking shelves - scanners pick out incoming titles that are destined for other users, placing these titles into a sorted outbound pile with a new, appropriately addressed red envelope. Netflix not only helps out the postal service by picking up and dropping off the DVDs at its hubs, it pre-sorts all outgoing mail for faster delivery. This extra effort has a payoff – Netflix gets the lowest possible postal rates for first-class mail delivery.First-class mail takes only one day to be delivered within a 50-mile radius, so the warehouse network allows Netflix to service over 97 percent of its customer base within a two-day window – one day to get in, early the next morning to process the next item in their queue, with arrival of that new title at the customer's address by that afternoon. Netflix usa vpn outside iphone That means a customer with the firm's most popular 'three disk at a time' plan could watch a movie a day and never be without a fresh title
Monday, March 19, 2012
incoming VPN connections
Here, we present some preliminary measurement results from our ,prototype. The network set-up for the measurement is shown in ,Figure 7. We have used NetIQ's Chariot for the measurements. ,Basically, the server provides both FTP and video (with 1.448 ,Mbps CBR streaming over RTP/UDP) services to a client across ,an AP implementing the dual queues. The console is the entity ,needed for Chariot in order to measure the network performance. ,Figure 7. Network set-up for the experiments ,Table 3. Performance comparison between the original AP ,and a modified AP with two queues ,Comparison ,Original ,Two ,queue ,Gain ,TCP 3.851 3.703 -3.84%,Throughput ,RTP 1.448 1.448 0.00%,Avg. 2.9 2.6 -10.34%,Max. 4.0 3.0 -25.00%,Jitter of ,RTP ,Min. 2.0 2.0 0.00%,Avg. 30.7 20.2 -34.20%,Max. 32.0 23.0 -28.13%,One-way ,delay of ,RTP ,Min. 30.0 18.0 -40.00%,Table 3 shows the measurement results for a number of ,performance parameters. First of all, we observe that the one-way ,delay of RTP (or RT traffic) is reduced by over 30%. This at least ,verifies that our goal is achieved via this simple modification of the device driver. The jitter of RTP is a bit improved as well. In ,case of throughput, we observe that there is no change with the ,RTP throughput as it should be is the case with a CBR traffic, but ,the TCP (or FTP traffic) throughput is a bit reduced. We predict ,that this happens due to an increased delay of the FTP traffic out ,of the priority queuing of the modified device driver. ,4.4 Limitations and Future Work ,The priority queuing implemented currently achieves a ,prioritization among different types of frames, thus achieving a ,lower delay for RT traffic. However, this approach is limited in a ,number of ways. First, even if there are dual queues in the device ,driver, there is a single FIFO inside the MAC controller, and we ,cannot do any scheduling of the frames once a frame is forwarded ,to the MAC controller. Second, for the actual medium contention, ,every device including the AP contends in a fair manner based on ,the 802.11 CSMA/CA. Therefore, for example, a RT frame in an ,AP and a NRT frame in a terminal contend with the same channel ,access rule. Accordingly, in certain situations, the performance of ,the proposed scheme will be severely compromised. For example, ,if a terminal transmits a large amount of data, the scheduling ,within the AP explained above may not be that effective. ,Currently, we are investigating a class of algorithms to handle this ,problem. ,Independent from the scheduling algorithm itself, we need more ,experiments as well. For example, we will need to check the VoIP ,performance with more contending terminals. Once we are ,assured that a reasonable performance based on this software ,queue implementation is achieved, we are planning to implement ,this approach into the existing APs of NESPOT to enhance the ,VoIP services as well as a potential VoD service.,
Sunday, March 18, 2012
N2N community vpn
• N2N node membership is rather static. Nodes usually register with a N2N community and stick with it as long as the node is operational. In other networks such as Gnutella or Napster the membership change rate is much higher and can lead to issues as the network topology might need to be changed in order to handle new members.• N2N nodes themselves do not store, cache, replicate or manage any content. This is because N2N connects network peers rather than content and consumers.• The goal of N2N is not to share files but rather to allow peers to communicate generically in a secure way and to locate each other by consistent addressing regardless of their physical network location. Data sharing is accomplished by higher layer protocols as the Internet design intended.3. N2N Architecture and ImplementationEdge nodes run on a host that can be placed in a private or public LAN. Supernodes are used to introduce edge nodes and relay packets to an edge behind symmetrical NAT (which prevents it from being directly reachable by peers). With symmetric NAT all requests from the same internal IP:port to a specific IP destination:port are mapped to an external IP:port. If the same internal host sends a request with the same source address and port to a different destination, a different external mapping is used.
Saturday, March 17, 2012
VPN WISH IWCM prototype
When integrated with a UE device's network protocol stack, the IWCM provides standards-compliant(3GPP, 3GPP2, WiMAX, Wi-Fi) and service providerpolicy-based functionality that enables seamless andtransparent session and service continuity on intertechnology handovers to IP-based VoIP, video, anddata applications.We introduce this section by describing the UEside procedures for seamless inter-technology handover. Next, we present an overview of the IWCMreference architecture, followed by a more detaileddescription of its components.The WISH IWCM prototype, available at BellLabs, is used for a variety of customer demonstrations,trade shows, and ongoing research work.
Thursday, March 15, 2012
MPLS aim to offer advanced IP network VPN
To meet high-level demands of security and efficiency in the backbone networks, MPLS aim to offer advanced IP network TE mechanisms these will facilitate the ISPs for easily evaluating, examining and meeting a variety of their service necessities a-cross the backbone. By the use of intelligent routers and speedy switches MPLS provides a technique for mapping IP segments with connection-based transport (such as frame relay or ATM) more efficiently. This supports the QoS definition inside the header of MPLS (Rosen et al., 2001; Rosen et al., 1999) as well. Using routing statistics of layer 3, MPLS distributes resources and builds forwarding tables for routing, while it utilizes layer 2 for switching or forwarding the information through the right link or route. Each IP packet includes a label of MPLS which is subsequently linked with a specific entry inside the forward routing table that identifies the upcoming hop. The network-flows with similar requirements for level of service and routing decisions, commonly keep the same pathway/route across the network resulting in a consistency of service-level for network-flows which having higher priority. MPLS is required to deploy the Label Switching Routers (Das et al., 2003) in the networks that will affect the momentum whereupon MPLS based solution is deployed. At the moment, MPLS is at target in favor of deployment in the backbones first.
Wednesday, March 14, 2012
VPN software for all hardware and software platform
How this VPN works is of the following: For instance, if the Australian branch in Sydney decides to contract a supplier, then the London office might need to know that immediately. The main part of IT infrastructure is set up data hosted on Seoul. In Singapore there are twenty people whose work depends on the availability of the data hosted on Seoul servers. The said scenario is depicted in Figure 2. Both sites are equipped with a permanent Internet line. An internet gateway router is set up to provide Internet access for the staff. This router is configured to protect the local network of the site from unauthorized access from the other side, which is the "culprit"Internet. Such a router set up to block special traffic san be called firewall and must be found in every branch that is supposed to take part in the VPN. The software used for VPN must be installed on this firewall. Many modern firewall appliances from manufacturers like Bin Tec or Cisco includes this feature and there is VPN software for all hardware and software platform. Once connection has been established, the company has a working Virtual Network. The two branches are connected via internet and can work together in a real network. Here, a VPN without privacy, because any internet router between Seouland Singapore can read the data exchanged. A competitor gaining control over an internet router could read all relevant business data going through the virtual network.
This is, in fact, the most common type of VPN –
Gathering Information You Need
Monday, March 12, 2012
adaptive VPN unblock internet
In this paper, we describe a new mechanismwhich we call an adaptive VPN that enables enterprises to selectively transport some packets from/to auser on an end-to-end VPN session and at the sametime transport other packets from/to the same useron a network-based VPN session, based on the application that is accessed by the user. This mechanismprovides enterprises the flexibility to enjoy the bene-fits of a network-based VPN for any user/applicationcombination that the enterprise is willing to entrust tothe NSP. At the same time, enterprises can transport data that requires a higher level of security usingend-to-end VPNs. This flexibility increases theacceptability of network-based VPNs to enterprises,thereby increasing the NSP's revenue opportunities.Adaptive VPN is illustrated in Figure 4
Different types of VPN
Our QoS model allows three types of VPNs as describedbelow.Type 1-static VPNs: For this kind of VPN, some preallocated dedicated or shared lightpaths are established tomeet its traffic needs. Traffic needing this type of servicenormally has a constant bit rate and require high servicequality, in terms of end-to-end delay and jitter. Staticlightpaths are for CBR traffic streams only and not forVBR or UBR/ABR traffic streams, even if there is no CBRtraffic on the static lightpaths. This will be the mostexpensive service due to the static lightpaths. Of course,within one VPN traffic matrix, there will be only a fewtraffic demands needing this type of service. Since there maybe several VPN traffic streams sharing the static lightpaths,it is necessary to have a scheduling mechanism in the buffersat the access nodes. A sophisticated scheduling mechanism,such as weighted fair queue can be adopted in thisframework. However, to simply illustrate the framework,we adopt a simple round-robin scheme here. In the nonbuffer scenario, a first come first serve principle is adopted.Type 2-OBS VPNs: For this kind of VPN, a set oflightpaths are provided that are established only whentraffic streams have the connection requirement. This kindof traffic stream is more likely to be generated by webbrowsers, wide area TCP connections and variable-bit-rate(VBR) video sources. These traffic streams are bursty.Lightpaths are established using optical burst switching(OBS). OBS sends a control packet first on a separatechannel, then waits for an offset time called just enoughtime (JET) [8], than the burst data packet is sent out. Afterthe burst data packet passes the link, the wavelengths arereleased.Type 3-alternative lightpath VPNs: For this kind of VPN, adynamic lightpath is setup when there is a traffic connectionrequirement. The lightpath setup uses a two-way reservationmethod, which introduces a long propagation delay wheninitialising the lightpath. Because of the delays involved inidentifying a path and is acknowledgement, this method issuitable for VPNs which have less stringent QoS requirements, e.g. UBR or ABR traffic streams.In this paper we study the performance of VPNs ofdifferent types. We examine the performance under twoscenarios: with buffers and without buffers in the accessnodes. In the scenario with buffers, we examine the delayfor the different types of VPN traffic streams. In the nonbuffer scenario we examine the blocking probability for thedifferent types of VPN traffic streams.For the static lightpath, we need a long-term trafficpattern and use a heuristic algorithm to set up the staticlightpaths. For the OBS lightpath, we follow a first comefirst service procedure to set up the lightpath for them. Ifthere are more than two traffic connection requirements atthe same time, the one with the heavier traffic loading is setup first. In the OBS lightpath, the data packets use only thedeterministic path to transfer. For the alternative lightpath,we use a two-way reservation scheme to set up the lightpathwhen the traffic connection requirement occurs. We seek analternative path if the deterministic path is not available.The latter two types of VPN can handle dynamic trafficstreams. Depending on the different QoS requirements, wedeploy OBS or the alternative scheme for different trafficstreams.
Tuesday, March 6, 2012
How Does Netflix Ban You in Indonesia?
How Does Netflix Ban You in Indonesia?
If you are new to Netflix, again you should apperceive that Netflix detects your area through your IP address. IP Abode is a actual different amount which your Internet Service Provider (ISP) has accustomed you. So, with the advice of the IP Address, the servers at Netflix will apperceive that what country you are advancing from. So, Netflix will apperceive that you are not amid in US and you will not be able to assurance up.
Monday, March 5, 2012
An Internet Protocol address (IP address)
Provide secure VPN encrypted tunnel protocol:
By blocking the interception and packet sniffing confidential, allo wing sender authentication,to prevent identity spoofing
Message integrity, to prevent the alteration of the message
Secure VPN protocols include the following:
IPSEC (Internet Protocol Security) by the Internet Engineering Task Force (IETF), initially for IPv6, which requires developed countries. This standards-based security protocol widelydistressed IPv4. Layer 2 Tunneling Protocol over IPsec operation. It is designed to meet thesecurity objectives are: authentication, integrity, and confidentiality. An IP packet summary and IPsec functionality to encrypt results together with the surrounding mob.
Transport Layer Security (SSL / TLS) is the cancer of the tunnel network traffic, because it isthe OpenVPN project, or a separate connection. Many vendors to provide remote accessthrough SSL VPN functionality. Failure run of the place in an SSL VPN connection to cancerelsewhere IPsec network address translation and firewall rules.
Datagram Transport Layer Security (DTLS), ice Distressed Cisco AnyConnect VPN to solve the problem, through the UDP tunnel SSL / TLS speed.
Microsoft Point to Point Encryption (MPPE) with their point of view, point-to-point tunneling protocol and compatible with other platforms of several of the migration.
Microsoft's Secure Socket Tunneling Protocol (SSTP), introduced in Windows Server 2008and inWindows Vista Service Pack 1. SSTP tunnel point Point to Point Protocol (PPP) orLayer 2 Tunneling Protocol flow through SSL3.0 channel.
Saturday, March 3, 2012
Set Up A VPN Connection in Windows 7
Set Up A VPN Connection in Windows 7
VPN stands for Virtual Private Network, a network that connects one or more computers to a large network, such as a business network, using the Internet. A VPN is encrypted and safe, so it's widely adopted by many of businesses. VPN is a pretty complicate network protocol that we are not going to discuss more deep in here. What I cover in this post is a simple how-to that simply shows the steps to set up a VPN connection in Windows 7.
First of all, please note that this how-to uses the built-in network setup right in Windows 7, so it works the best if VPN server on the other side is also from Windows Server.
Open up network and sharing center from Control Panel, and choose Set up a new connection or network.
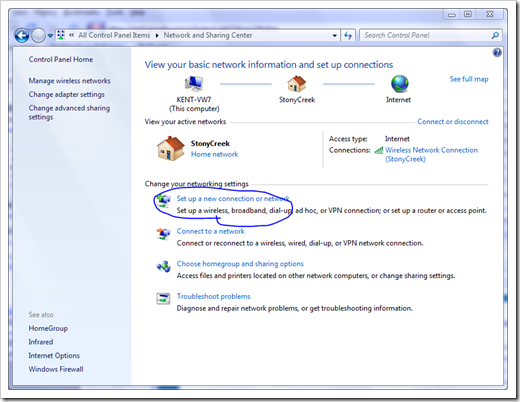
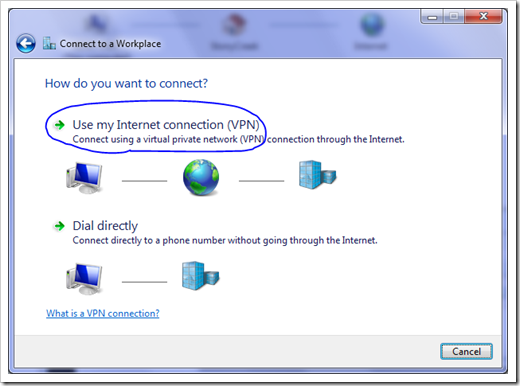
There are two options in the Connect to a Workplace window. 99% of the time you just need to pick the first option, unless your company only allows you to dial in using a phone line.
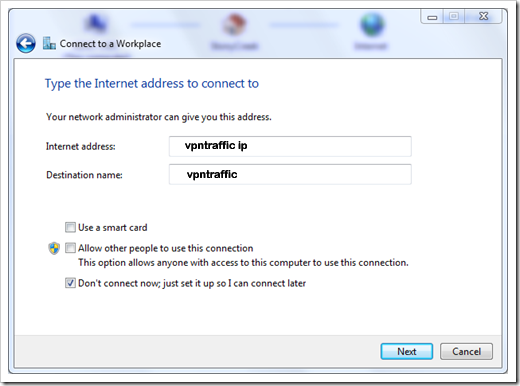
Type in the address in either domain name or IP address, and name the connection in the destination name box. And click Next.
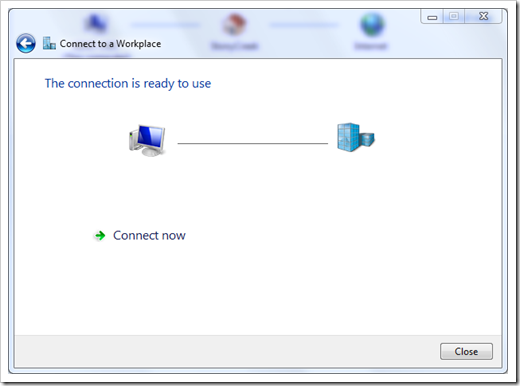
You can leave all user login info blank if you feel safe that way in the next window. And clickCreate. You're all set if you see the next window as below.
To launch it, simply click the small network icon on the system tray at the bottom right corner, and pick the connection we just created from the popup list, and connect.
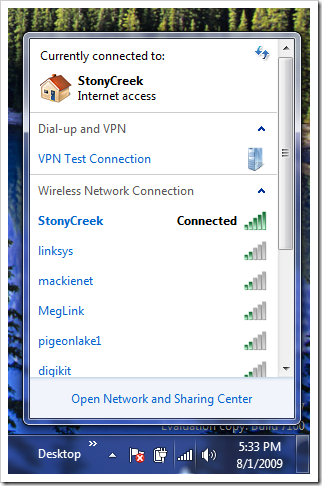
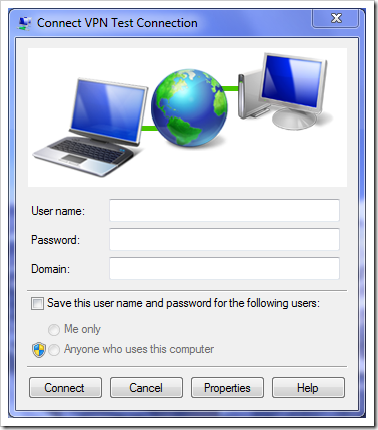
Type in your user name and password, and you are on your way connecting your Windows 7 to your company network.
Hope it helps, and enjoy.